Secure Shell (SSH) is a pivotal protocol for secure network connections, enabling safe data transmission over the internet. This comprehensive guide breaks down fundamental concepts of SSH, explores various use cases, delves into the utilization of PEM and PPK files, and discusses the reasons behind using these key formats, enhancing the versatility of SSH for beginners.
Understanding SSH
- Secure Connections
- SSH ensures secure communication by encrypting data, preventing unauthorized access, and maintaining data integrity.
- Remote Login
- SSH facilitates remote logins, empowering users to access and control computers or servers from a distance.
- Command Line Interface (CLI)
- SSH operates primarily through the command line, offering efficiency and flexibility in managing remote systems.
- SSH Keys
- SSH keys, consisting of private and public components, enhance security by replacing traditional password-based authentication.
- SSH Port
- The default port for SSH is 22, but users can change this for security reasons.
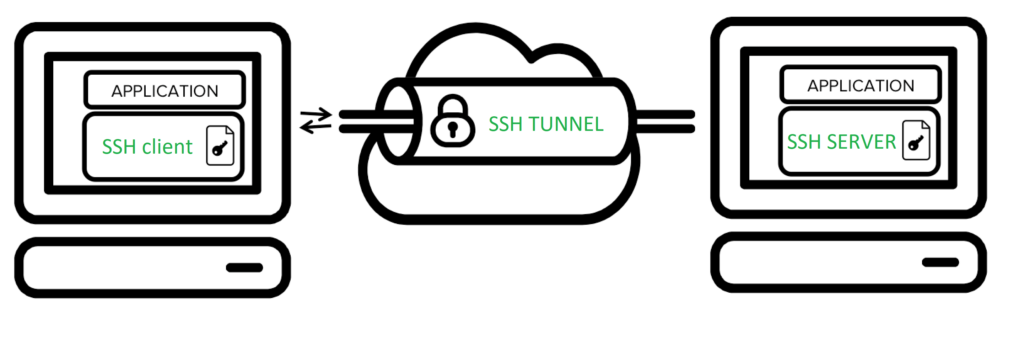
Common SSH Use Cases:
1. Remote Login:
ssh username@remote_server_ip - Logging into a remote server securely using SSH requires the appropriate username and IP address.
2. Secure File Transfer (SCP):
- Uploading a file to the server
scp local_file.txt username@remote_server_ip:/path/to/destination/- Downloading a file from the server
scp username@remote_server_ip:/path/to/remote_file.txt /local/destination/3. SFTP (Secure File Transfer Protocol):
sftp username@remote_server_ip - SFTP provides a secure and interactive way to transfer files between local and remote systems.
4. Backup and Restore (rsync):
- Backing up data to the server:
rsync -avz /local/path/ username@remote_server_ip:/remote/path/- Restoring data from the server:
rsync -avz username@remote_server_ip:/remote/path/ /local/path/- Rsync is a versatile tool used for efficiently synchronizing and transferring files between systems securely.
5. Secure Database Connection:
- Connecting to a remote MySQL database via SSH:
ssh -L 3306:localhost:3306 username@remote_server_ip -N- SSH tunneling enhances database security by creating a secure channel for data transmission.
6. Using Git Securely:
- Employing SSH with Git involves setting up SSH keys and utilizing SSH URLs when cloning or interacting with repositories, ensuring secure version control practices.
Utilizing SSH with PEM and PPK Files:
1. Generating SSH Key Pair (PEM):
ssh-keygen -t rsa -b 2048 -f key.pem- This creates a private key (key.pem) and its corresponding public key.
2. Connecting with PEM Key:
ssh -i key.pem username@remote_server_ip3. Converting PEM to PPK (PuTTY Key) Format:
puttygen key.pem -o key.ppkThis converts a PEM private key to PPK format compatible with PuTTY.
4. Connecting with PPK Key (PuTTY):
- Open PuTTY and provide the server IP, port, and the PPK file under “Connection” > “SSH” > “Auth.”
- Connect to the server securely using PuTTY with the converted PPK key.
Reasons for Using PEM and PPK Files:
1. Enhanced Security:
- PEM and PPK files use asymmetric cryptography, providing a more secure authentication method than traditional passwords.
2. Compatibility Across Platforms:
- PEM keys are widely used in Unix-based systems, while PPK keys are compatible with PuTTY on Windows. This ensures seamless cross-platform access.
3. Encrypted Private Keys:
- Both PEM and PPK formats support passphrase protection for private keys, adding an extra layer of security.
4. Versatility in SSH Clients:
- PEM keys are widely supported by default in many SSH clients, while PPK keys cater to users employing PuTTY on Windows.
Examples of SSH Use Cases with PEM and PPK:
1. SCP with PEM Key:
- Uploading a file to the server
scp -i key.pem local_file.txt username@remote_server_ip:/path/to/destination/- Downloading a file from the server
scp -i key.pem username@remote_server_ip:/path/to/remote_file.txt /local/destination/2. Using SFTP with PEM Key:
sftp -i key.pem username@remote_server_ip3. Backup with Rsync and PEM Key:
- Backing up data to the server:
rsync -avz -e "ssh -i key.pem" /local/path/ username@remote_server_ip:/remote/path/- Restoring data from the server:
rsync -avz -e "ssh -i key.pem" username@remote_server_ip:/remote/path/ /local/path/4. PuTTY for Windows (PPK):
- Use PuTTY with the converted PPK key for secure SSH connections on Windows.
Considerations
1. Security Measures
- Protect PEM and PPK files with strong passwords for added security.
- Limit access to key files to authorized users.
2. Key Management
- Regularly rotate and update SSH keys, both in PEM and PPK formats.
- Store keys securely and consider using passphrase-protected keys.
3. Compatibility
- Understand the compatibility of PEM and PPK keys with different SSH clients.
4. File Permissions
- Ensure appropriate file permissions for key files to prevent unauthorized access.
Conclusion
SSH, with its ability to work seamlessly with PEM and PPK key formats, offers flexibility and compatibility across various platforms. Whether generating key pairs, converting formats, or securely connecting to servers, understanding how to use PEM and PPK files enhances the versatility of SSH, making it an even more valuable tool for secure remote communication and data transfer. The use of these key formats further strengthens the security posture of SSH, providing robust and reliable protection for sensitive data and remote access.
Explore more fascinating blog posts on our site!
SSH is an important component in the deployment process. Do you have any ideas for using SSH effectively? Please share your thoughts! Thank you for reading this post.